Securing Clawbot: Protect Your Open Ports
I've been there—staring at a Clawbot instance with ports wide open, feeling the chill of potential security breaches. So, how did I secure my setup and avoid costly mistakes? Let's dive into Clawbot vulnerabilities, from prompt injections to weak skill validations. First, I shut those darn open ports. Then, I beef up skill validations to prevent Clawbot from doing things it shouldn't. But watch out for prompt injection attacks—they're sneaky and Anthropic isn't shy about banning accounts. I share my steps to audit your Clawbot system's security and protect your digital assets efficiently.
I've been there—staring at a Clawbot instance with ports wide open, feeling the chill of potential security breaches. That's when I thought, 'I need to lock this down, fast.' The truth is, Clawbot systems, as powerful as they are, come with a host of vulnerabilities. I started by addressing those 754 open ports anyone can find on shodan.io. Next, I beefed up my Clawbot's skill validation—you don't want it doing things it shouldn't. And then, there are prompt injection attacks. Trust me, they can be costly (and not just the $500 from malicious emails). We'll also talk about conducting security audits and the potential consequences, like Anthropic account bans tied to misuse. I'll walk you through my approach to securing Clawbot with concrete actions.
Understanding Open Ports and Security Risks
Open ports are like leaving doors ajar on your network. It's akin to leaving your house door unlocked when heading to work. I discovered 754 Clawbot instances with open ports on shodan.io, and that was a real eye-opener about the potential for attacks. Each open port is a potential invitation for cyberattacks, allowing intruders to access sensitive information like API keys or conversation history.
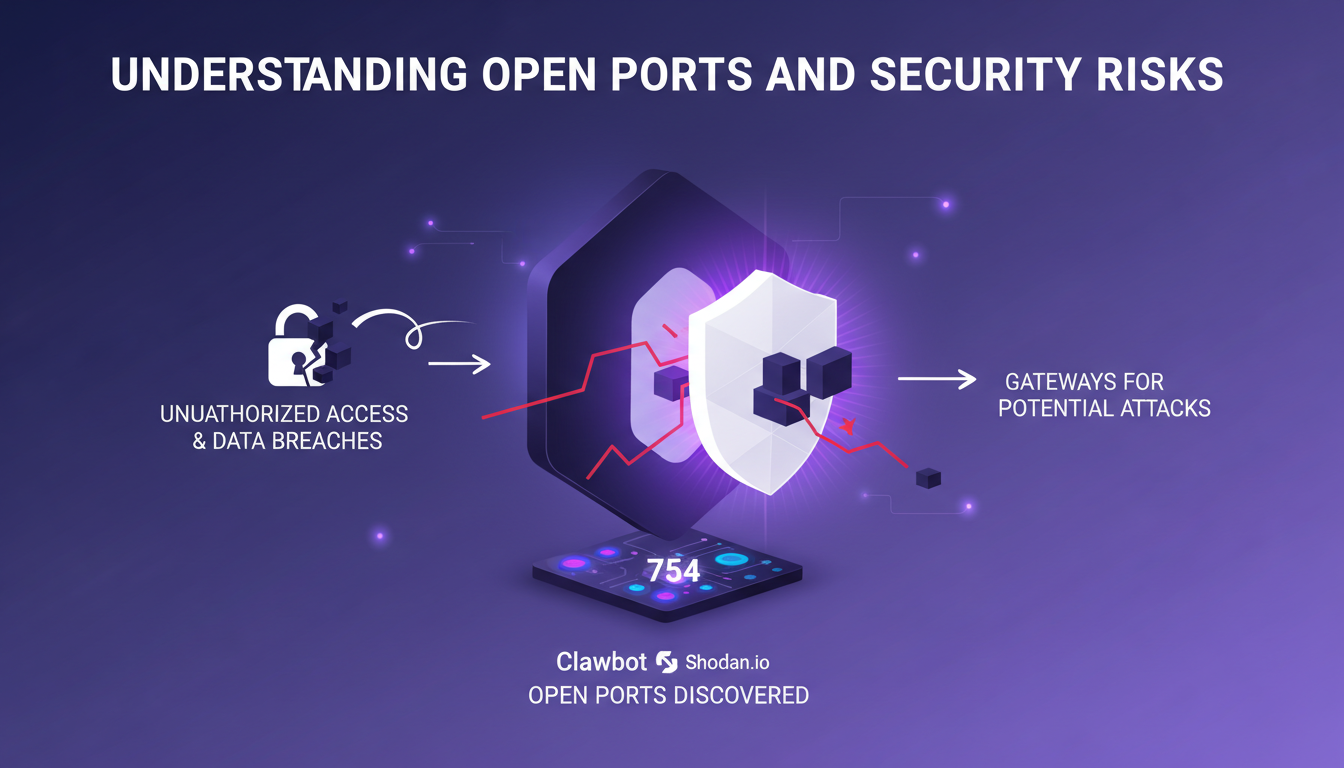
The first step to securing your system is mapping your network to identify these open ports. I use tools like Nmap to scan and close those that aren't necessary. It might seem tedious, but believe me, it's a crucial step for reinforcing security. Better safe than sorry when it comes to IT security.
- 754 Clawbot open ports detected on shodan.io.
- Unauthorized access can lead to data breaches and security violations.
- Mapping and scanning your network is the first step to securing your systems.
Mitigating Vulnerabilities in Clawbot Systems
Prompt injection attacks can manipulate Clawbot responses. This type of attack can be as simple as adding a malicious instruction in a message. To counter this, I've implemented input validation to filter out malicious data. But watch out, you need to balance security and performance.
Next, I started using sandboxing for Clawbot skills. This technique prevents unauthorized actions by isolating processes. However, be cautious, as this can slow down your systems, so weigh the pros and cons. Finally, keeping your systems updated with the latest security patches is crucial.
- Prompt injection attacks can be avoided with strict input validation.
- Sandboxing skills prevents unauthorized actions.
- Watch out for performance trade-offs when using sandboxing.
Validating Clawbot Skills and Defensive Models
Skill validation ensures that Clawbot performs as expected. I use defensive programming to anticipate and handle errors. This means coding in a way that prevents errors before they occur. For me, defensive models against prompt injection are a must. It's a delicate dance where you must balance security and responsiveness.
Peter Clawbot's tips have been immensely helpful in this process. He emphasizes the importance of rigorous validation and regular updates of skills.
- Skill validation is key to ensuring correct performance.
- Defensive programming helps anticipate and manage errors.
- Balancing security and responsiveness is crucial.
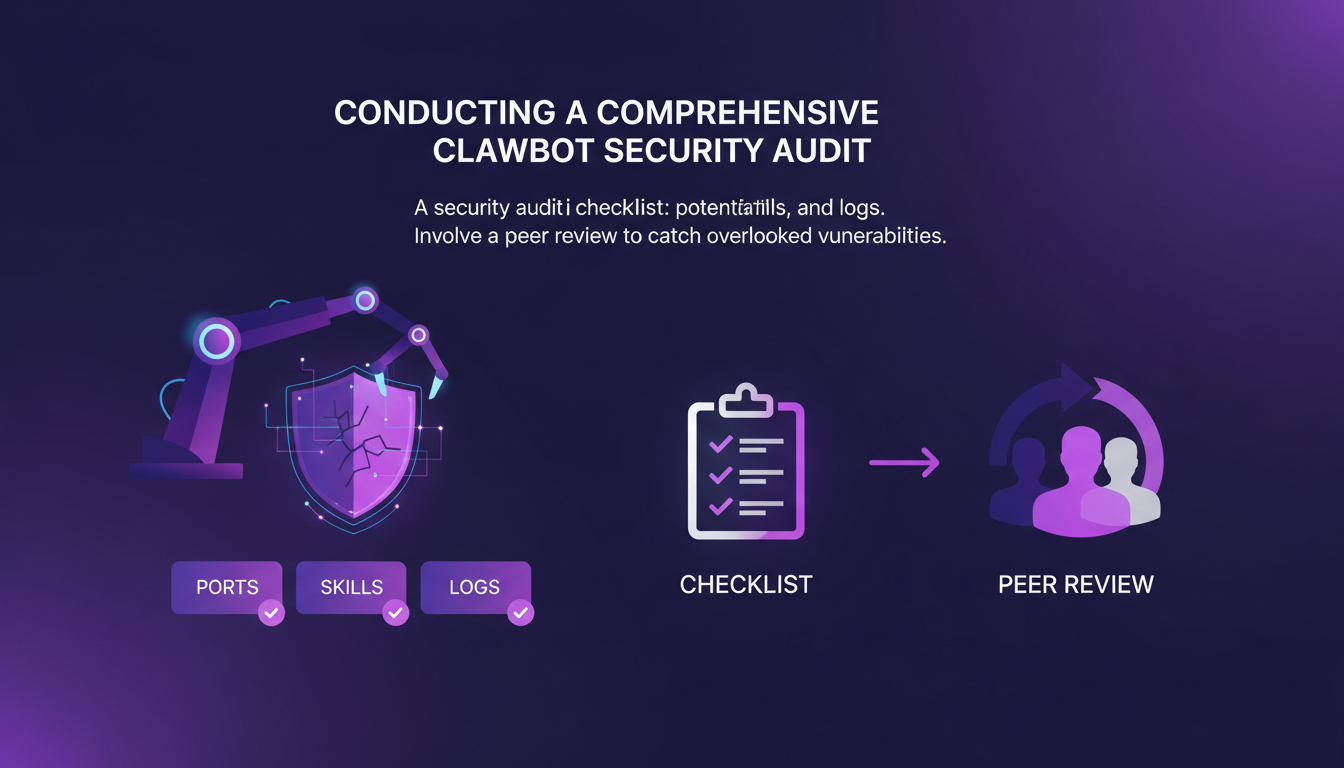
Conducting a Comprehensive Clawbot Security Audit
A security audit identifies potential weaknesses. I always start with a checklist: checking ports, skills, and logs. It's essential to involve a peer review to catch vulnerabilities you might have overlooked. Documenting your findings and planning regular audits is a must.
Consider the potential business impact of breaches. A breach could cost dearly, not just financially but also in reputation. Never underestimate the importance of a security audit.
- Start with a checklist: ports, skills, logs.
- Peer review can reveal hidden vulnerabilities.
- Document and plan regular audits.
Handling Anthropic Account Bans and Compliance
Account bans can severely disrupt operations. I learned to understand the terms of service to avoid violations. Monitor usage patterns to stay compliant and promptly address any flagged activities to prevent bans.
Regular compliance checks can save you from costly errors. Once again, better safe than sorry. Don't let compliance violations compromise your operation.
- Understanding terms of service is crucial to avoid violations.
- Monitor usage patterns to stay compliant.
- Regular compliance checks can prevent costly errors.
Securing your Clawbot systems isn't just about closing ports. It's a comprehensive strategy. First, start with a system audit to spot the 754 open ports visible on shodan.io. Then, validating every Clawbot skill helps fend off injection attacks, which could hit you for $500 in damages if neglected. Finally, integrating compliance standards is key to smooth operations.
- Takeaway 1: Regularly audit to identify open ports (like the 754 found on Shodan).
- Takeaway 2: Validate and test Clawbot skills to mitigate injection risks.
- Takeaway 3: Adhere to compliance standards for seamless operation.
These strategies are a real game changer for protecting your operations, but don't forget the ongoing patch management and updates.
Ready to secure your Clawbot setup? Start with an audit today. For a deeper dive, watch the video "The Clawdbot Threat and your Fixes!" on YouTube. It's like having a chat with a colleague who's navigated these challenges before.
Frequently Asked Questions

Thibault Le Balier
Co-fondateur & CTO
Coming from the tech startup ecosystem, Thibault has developed expertise in AI solution architecture that he now puts at the service of large companies (Atos, BNP Paribas, beta.gouv). He works on two axes: mastering AI deployments (local LLMs, MCP security) and optimizing inference costs (offloading, compression, token management).
Related Articles
Discover more articles on similar topics
Kimmy K2.5: Mastering the Agent Swarm
I remember the first time I dove into the Kimmy K2.5 model. It was like stepping into a new AI era, where the Agent Swarm feature promised to revolutionize parallel task handling. I've spent countless hours tweaking, testing, and pushing this model to its limits. Let me tell you, if you know how to leverage it, it's a game-changer. With 15 trillion tokens and the ability to manage 500 coordinated steps, it's an undisputed champion. But watch out, there are pitfalls. Let me walk you through harnessing this powerful tool, its applications, and future implications.
Ollama Launch: Tackling Mac Challenges
I remember the first time I fired up Ollama Launch on my Mac. It was like opening a new toolbox, gleaming with tools I was eager to try out. But the real question is how these models actually perform. In this article, we'll dive into Ollama Launch features, put the GLM 4.7 flash model through its paces, and see how Claude Code stacks up. We'll also tackle the challenges of running these models locally on a Mac and discuss potential improvements. If you've ever tried running a 30-billion parameter model with a 64K context length, you know what I'm talking about. So, ready to tackle the challenge?
Clone Any Voice for Free: Qwen TTS Revolutionizes
I remember the first time I cloned a voice with Qwen TTS—it was like stepping into the future. Imagine having such a powerful tool, and it's open source, right at your fingertips. This isn't just theory; it's about real-world application today. Last June, Qwen announced their TTS models, and by September, the Quen 3 TTS Flash with multilingual support was ready. For anyone interested in voice cloning and multilingual speech generation, this is a true game changer. With models ranging from 0.6 billion to 1.7 billion parameters, the possibilities are vast. But watch out, there are technical limits to be mindful of. In this article, I'll guide you through multilingual capabilities, open-source release, and emotion synthesis. Get ready to explore how you can leverage this tech today.
AI's Transformative Impact on Software Engineering
I vividly remember the first time I integrated AI into my software engineering workflow. It felt like moving from a bicycle to a jet. But let's be honest, it's not all smooth sailing. Navigating AI's transformative impact requires overcoming user adoption hurdles and understanding the trade-offs between generalized and specialized models. In the OpenAI Town Hall with Sam Altman, we dive into how AI is revolutionizing software engineering, the challenges, and the real gains in efficiency and cost. From cost reduction to personalization and deflationary economic impacts, it's about steering this tech smartly. But watch out, every technical choice comes with its own limits and constraints. Let's dive into what's genuinely useful and what's just noise.
Measuring Dev Productivity with METR: Challenges
I've spent countless hours trying to quantify developer productivity, and when I heard Joel Becker talk about METR, it hit home. The way METR measures 'Long Tasks' and open source dev productivity is a real game changer. With 2030 looming as the potential year where compute growth might hit a wall, understanding how to measure and enhance productivity is crucial. METR offers a unique lens to tackle these challenges, especially in open source environments. It's fascinating to see how AI might transform the way we work, though it has its limits, particularly with legacy code bases. But watch out, don't overuse AI to automate every task. It's still got a way to go, especially in robotics and manufacturing. Joel shows us how to navigate this complex landscape, highlighting the impact of tool familiarity on productivity. Let's dive into these insights that can truly transform our workflows.